EUDI Wallet Acceptance for Enterprise IAM (2025–2027): A 90-Day Blueprint
November 6, 2025 by Nick Morgan
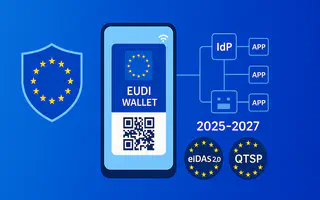
EUDI Wallets are state-backed digital identity wallets defined under eIDAS 2.0 to let users authenticate, assert attributes, and sign with high assurance across borders